Setting Up CAC (Common Access Card)
When a CAC, Common Access Card, is used, you can set the portal to allow access without the client CAC user entering a user name and password.
To configure the portal servers for CAC authentication:
1 Log in to the CTERA Portal master DB server as root, using SSH.
2 Copy the root certificate file associated with the CAC certificate and any intermediate certificates in the chain to the /root/ path of the Master DB Server.
3 Create the truststore.
a In the Master DB Server and enter the following commands: . $bindir/ctera-common.sh ; export _JAVA_OPTIONS
b Move to the /usr/local/ctera/apache-tomcat/webapps/ directory and run the following keytool commands for the CAC certificate file and any intermediate certificates in the chain. For example, for a CAC certificate file named RootCA1.cer and an intermediate certificate named IntermediateCA1.cer, run the following two commands, changing the jdk1.8.0_201 value to the JDK on the server (use the command ls -d /usr/local/ctera/jdk*/bin to find the current JDK bin directory):
/usr/local/ctera/jdk1.8.0_201/bin/keytool -import -keystore truststore -file /root/RootCA1.cer -alias rootca1 -trustcacerts -deststorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg)
/usr/local/ctera/jdk1.8.0_201/bin/keytool -import -keystore truststore -file /root/IntermediateCA1.cer -alias intermediateca1 -trustcacerts -deststorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg)
Note: The alias name of each certificate in the keytool command must be unique.
You can display the certificates in the truststore with the following command:
keytool -list -v -keystore truststore -deststorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg)
c Convert the truststore format to BCFKS format by running the following command, changing the jdk value to the JDK on the server:
keytool -importkeystore -srckeystore /usr/local/ctera/apache-tomcat/webapps/truststore -srcstoretype JKS -destkeystore /usr/local/ctera/apache-tomcat/webapps/truststore.bcfks -deststoretype BCFKS -srcprovidername "SUN" -providerclass com.safelogic.cryptocomply.jcajce.provider.CryptoComplyFipsProvider -providerpath /usr/local/ctera/jdk1.8.0_201/jre/lib/ext/SafeLogic_CTERA.jar -srcstorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg) -deststorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg)
You can display the entries in the new BCFKS keystore with the following command:
keytool -list -v -keystore truststore.bcfks -storetype BCFKS -deststorepass $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg)
The password is the SERVER_KEY, which is extracted automatically from /etc/ctera/portal.cfg and used in the following part of above command $(grep -o -P "(?<=SERVER_KEY=).*" /etc/ctera/portal.cfg).
d Copy the truststore.bcfks file to the same path of the Replication DB server and all the portal servers, such as the application and preview servers. For example, using SCP, run the following command:
scp truststore.bcfks root@portal_ip_address:/usr/local/ctera/apache-tomcat/webapps
4 Enable FIPS by running the following in the command line: set /settings/javaSecurityProviderMode FIPS
5 Restart the portal servers.
To configure CAC single sign-on in the portal user interface:
1 In the global administration view, select Settings in the navigation pane.
2 Select SSO under USERS in the Control Panel page.
The Single Sign On window is displayed.
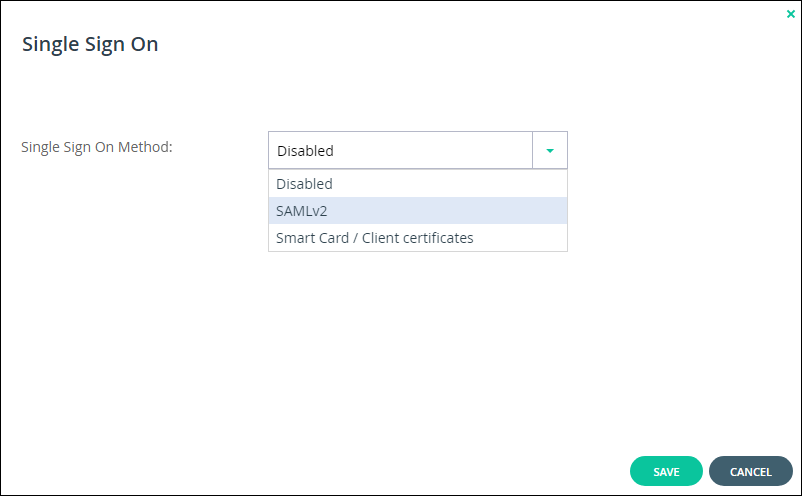
3 Select Smart Card / Client certificates from the drop-down box.
The Single Sign On window is redisplayed for CAC authentication.
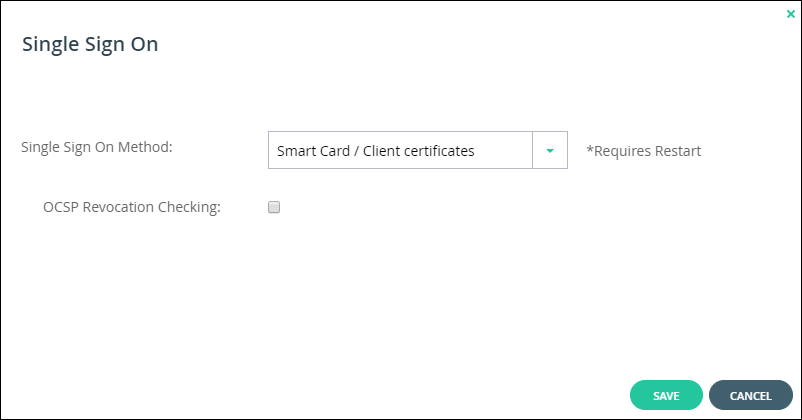
4 Uncheck OCSP Revocation Checking, unless an OCSP server is being used for certificate revocation and it returns an answer.
5 Click SAVE.
The portal servers are restarted.
Users log on to their systems using CAC.