Today, we’re excited to share that CTERA is launching CTERA Vault – our Write Once, Read Many (WORM) protection technology. As the latest addition to CTERA’s security suite, CTERA Vault protects against risks related to data tampering.
In simple terms, CTERA Vault allows data to be written to a storage system once and then prevents any modifications and/or deletions. Think of it as a security vault for your data that is immune to ransomware, accidental deletions, and unwanted changes.
The need for WORM technology arises from various factors. First and foremost, it helps organizations meet compliance requirements set forth by regulatory bodies and industry standards. Many sectors, such as finance (e.g., Financial Industry Regulatory Authority rules), healthcare (e.g., Health Insurance Portability and Accountability Act), and legal (e.g., electronic discovery and court admissibility), impose stringent regulations on data retention, protection, and auditability. CTERA Vault aids enterprises in guaranteeing the preservation and non-tampering of their data, while also ensuring compliance with data regulations through strict enforcement.
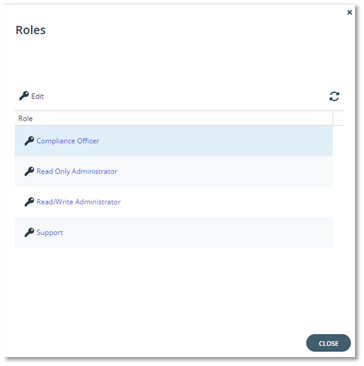
A new role, Compliance Officer, is used to manage any compliance-related tasks:
Moreover, CTERA Vault addresses the ever-growing challenge of data tampering and unauthorized modifications. Traditional storage systems are vulnerable to unauthorized alterations, either accidental or deliberate, which can compromise the accuracy and reliability of stored data. With CTERA Vault, organizations can prevent unauthorized changes, creating a permanent record that can be trusted and relied upon for critical decision-making processes.
WORM technology helps combat data loss due to accidental or malicious deletions. As data volumes continue to soar, the risk of unintentional data loss or intentional data sabotage grows. CTERA Vault Cloud Folders’ Retention mitigates these risks by ensuring that once information is written, it cannot be erased or overwritten, protecting it from accidental or deliberate deletion attempts.
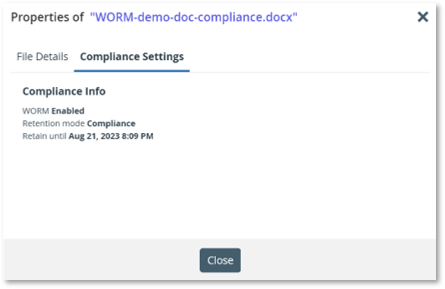
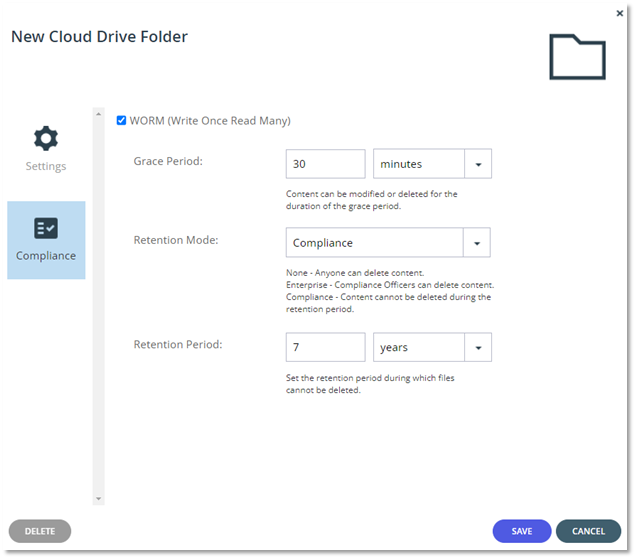
In the example below, a mission-critical Cloud Folder that must protect any data within it over 7 years is set. As a result, 30 minutes after writing the data into the folder, the data becomes immutable for a period of 7 years, without the possibility of changing this policy:
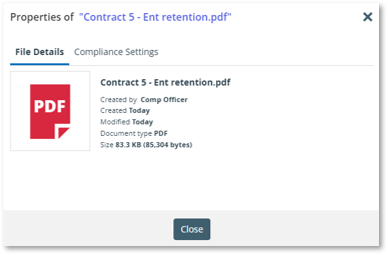
To assist a Compliance Officer with managing and monitoring WORM (and other) data in the portal, we have added an option to inspect the general and Compliance properties of a file or folder in the portal. The new interface can be accessed by any user from the Services Portal, although only a Compliance Officer will be able to access the Compliance tab. The File (or multiple files and folders) Details will provide information about the file’s owner, created and modified dates, format and size:
Multiple item selection will look as follows:
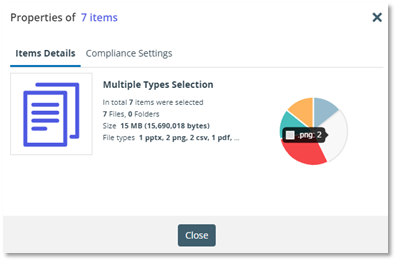
The Compliance Settings include the WORM status, retention mode, and Retain until dates:
If a user attempts, whether accidentally or intentionally, to perform an illegal action on a WORM-protected file, such as renaming, moving, modifying, or deleting it (assuming there is an active retention policy, such as Enterprise or Compliance), the system will trigger an error indicating that the action is rejected by the WORM policy. Simultaneously, the system will generate an audit log in the portal, and if available, on a syslog server.
Several industries can benefit from CTERA Compliance Vault data protection. Here are some examples:
- Financial Services: Banks, credit unions, investment firms, and other financial institutions handle sensitive customer data, financial records, transaction information, and regulatory compliance documents. WORM storage helps meet regulatory requirements (such as FINRA Rule 4511[c]) and provides protection against data tampering or deletion.
- Healthcare and Life Sciences: The healthcare industry deals with patient records, medical imaging data, clinical trial results, and research data. WORM technology ensures the integrity and long-term preservation of critical health information, supporting compliance with regulations like HIPAA (Health Insurance Portability and Accountability Act) and maintaining data for medical research and audits.
- Legal and Law Firms: Legal professionals require secure storage for legal documents, case files, contracts, and evidence. WORM data protection helps establish the authenticity and immutability of legal records, ensuring compliance with legal and regulatory requirements and preserving evidence for litigation purposes.
- Government and Public Sector: Government agencies, public institutions, and municipalities deal with vast amounts of sensitive and classified data, including citizen records, financial data, land records, and historical archives. WORM storage ensures data integrity, protects against tampering, and supports compliance with regulations governing data retention and security in the public sector.
- Manufacturing and Supply Chain: Manufacturing companies often need to retain product specifications, quality control data, and compliance records. WORM storage helps ensure the integrity of manufacturing data, preventing unauthorized modifications, and preserving crucial information for audits, recalls, and regulatory compliance.
In conclusion, CTERA Vault serves as a valuable solution for organizations seeking to enhance data security, integrity, and compliance. By implementing CTERA Vault, businesses can establish an immutable and tamper-proof data storage environment, meet regulatory obligations, safeguard critical information, and ensure the long-term preservation and availability of vital records. As the digital landscape continues to evolve, WORM technology stands as a robust defense mechanism against data tampering, unauthorized modifications, and accidental or malicious data loss, providing organizations with peace of mind and confidence in their data management practices.
-

Alex Berman is a tech enthusiast and Product Manager at CTERA Networks. With a bachelor’s degree in information systems management, he journeyed through tech support, NOC operations, and solutions architecture roles. At CTERA, he has grown from Support Engineer to Product Manager, steering innovation. He is a husband and father of two, and proudly resides in Raanana, IL, blending his passion for tech with the joys of family life.
Product Manager