How the shift from reaction and recovery to AI-powered proaction is making organizations safer.
Headlines of organizations falling victim to cyber-attacks are becoming all too familiar. And the scope, intent, and costs of the resulting damage are on a similarly alarming vertical trajectory.
The increasing frequency of attacks and the ongoing ‘arms race’ of nefarious malware toolsets are targeting organizations’ most valuable—yet most vulnerable—asset: human beings.
We are an intrinsically trusting species. Despite attempts by IT departments worldwide to pull out all the stops to train employees to be more scrutinizing, suspicious, and skeptical of malicious tactics and cybersecurity threats, it’s clear that user education is only one small (but essential!) part of a much larger cyber resiliency effort.
It’s no wonder that cybersecurity, with or without AI, is topping corporate IT investment plans in 2025.
Why are we seeing so many successful attacks?
To better understand this, let’s go through a standard attack timeline.
The five stages of a ransomware or exfiltration attack:
1. Detection
Organizations traditionally rely on a combination of desktop and server scanning products based on algorithms or signatures of reverse-engineered prior attacks. While this strengthens resiliency, it can often be easily bypassed when an unsuspecting user “holds the door open.” Read the latest example here.
Speaking plainly, organizations usually find out about a ransomware or exfiltration attack via the least desirable method, human detection.
By the time a user or admin visually notices the effects of an attack and reports it, the malicious tentacles are usually deep within your organization’s data as the costs of recovery continue to grow exponentially. Worse yet, an exfiltration attack may not leave any visual cues, keeping your organization in the dark until you’re contacted by the attacker and extorted or until your private data is found or sold on the dark web.
2. Remediation
The first priority in remediation should be shutting down the attack. The fastest way to do so is to start taking servers or shares offline so they can no longer be subject to attack. However, this means a halt in productivity. Once the situation is stabilized and there is confirmation that the attack is no longer progressing, logging is more closely analyzed to determine the source/scope of the attack. Then, efforts can shift to a more acute response. Meanwhile, your users are waiting to get back to work.
3. Recovery
This critical stage is when your organization decides whether they can rapidly or easily retrieve their data from a backup or else consider paying to unlock it to “get back to business” faster. How capable and quick the backup solution is in reverting data to its pre-modified state seriously impacts this decision. Succumbing to the attackers’ demands by paying ransom should be avoided at all costs as funding criminal organizations only emboldens and enables them to carry out future attacks on you and others.
4. Investigation
Conducting a post-mortem on the effects of this attack and how it was able to bypass your organization’s protections is critical to making key decisions on needed safeguards against future attacks. Your organization will also need to ascertain the extent of the damage, what data was affected and the type of sensitive information compromised.
5. Disclosure
This is the most dreaded step of all: the disclosure of the investigation to affected customers, partners, and any other individual or organization for which they may have been storing private data. If the investigation wasn’t able to clearly show which files were affected, it must be assumed that all of them were. Such information can have devastating business and reputational consequences once published. This step is important for fulfilling any legal or compliance requirements and can sometimes result in penalties.
So, what’s missing here?
Proactive Protection
Rather than waiting for late-stage detection—leading to panicked remediation, desperate recovery, a gruelling investigation, and an embarrassing disclosure to those affected (and perhaps the media at large)—organizations can instead adopt an AI-powered cybersecurity solution focused on real-time response. Think of a well-trained, omnipresent security force, waiting eagerly to identify and eject troublemakers from your organization’s data store.
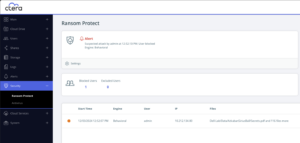
An intelligence solution trained on how businesses use file systems that can immediately detect attempts to encrypt or steal your data. Compromised access is terminated and quarantined in real-time as the attack begins, without disrupting other users (yay business continuity!). Simultaneously, your team is immediately alerted.
CTERA Ransom Protect with Honeypot not only stops the attack from progressing, it also automates the investigation by identifying the offending access and affected files. Additionally, it provides the ability to instantly revert to an unaffected version at the Edge, or in the Cloud.
In addition to Ransom Protect, CTERA provides these capabilities:
- CTERA Vault
Ensures data immutability, safeguarding files from tampering or deletion. - Global Namespace-Wide Antivirus
Provides comprehensive protection from Edge to Core. - CTERA Insight
Delivers advanced reporting tools for full transparency and control over your data.
While every measure to safeguard your data from attack is important, investments should be directed to those with the highest return, such as AI-powered security measures that proactively monitor and defend your data 24/7/365.
Always on, always watching, always protecting.
Contact CTERA today to find out how you can crush risk and protect your organization proactively.





















