Using Active Directory for Single Sign-On
You can configure single sign-on for a portal, for users defined in Microsoft Active Directory, using the Kerberos protocol. When single sign on is configured, CTERA Agents automatically and transparently authenticate to the portal using their Active Directory credentials, upon first login to the PC on which they are installed.
Note: Only one virtual portal can be defined with Kerberos.
A service principal name (SPN) account on Active Directory uniquely identifies an instance of a service. Before the CTERA Portal can use Kerberos authentication, you must register the SPN on the account object that the CTERA Portal uses to log on and then create a keytab file.
To configure Active Directory for single sign-on with CTERA Portal:
1 Get ctera-agent.adm from CTERA support.
Example ctera-agent.adm file:
CLASS MACHINE
CATEGORY !!CteraAgent
KEYNAME "Software\Policies\CTERA\Agent"
POLICY !!USESSO
EXPLAIN !!USESSO_Explain
VALUENAME "SSO"
VALUEON NUMERIC 1
VALUEOFF NUMERIC 0
PART !!SSO_Server EDITTEXT REQUIRED
VALUENAME "SSOServer"
END PART
PART !!SSO_Tip TEXT
END PART
END POLICY
END CATEGORY
[strings]
USESSO="Enable CTERA Agent automatic deployment"
USESSO_Explain="With this policy you can automatically deploy CTERA Agents.\n\n When this policy is disabled, or not configured, each CTERA agent must be manually connected to a CTERA portal or CTERA Cloud-Attached-Storage appliance.\n\n When this policy is enabled, the CTERA Agent installed on the computer automatically signs into the CTERA portal or appliance designated by the policy. When a user logs on to the machine for the first time, CTERA agent immediately signs into the designated server, using the credentials of that user."
SSO_Server="Sign into server"
SSO_Tip="Use the Fully-Qualified DNS name of a CTERA portal or a CTERA appliance. The target server must be a member of this Active Directory domain."
CteraAgent="CTERA Agent Settings"
2 In the Start menu on the server where Active Directory runs, select Administrative Tools > Group Policy Management.
The Group Policy Management console is displayed:
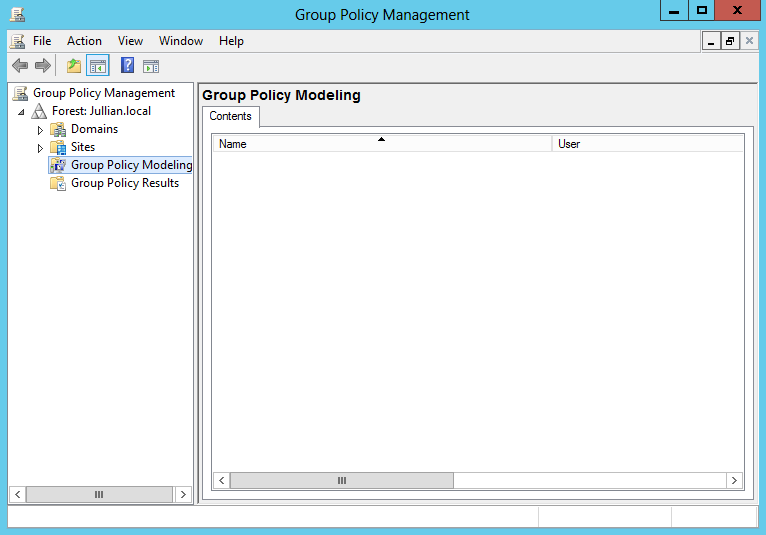
This console enables you to create domain-wide policies or policies for specific organizational units.
a In the navigation pane, drill-down to the domain or organizational unit for which you want to create the policy, right-click it and select Create a new GPO in this domain and Link it here.
The New GPO window is displayed.
b Enter a name for the policy and click OK.
c In the navigation pane, select the domain and in the right pane, select the Linked Group Policy Objects tab.
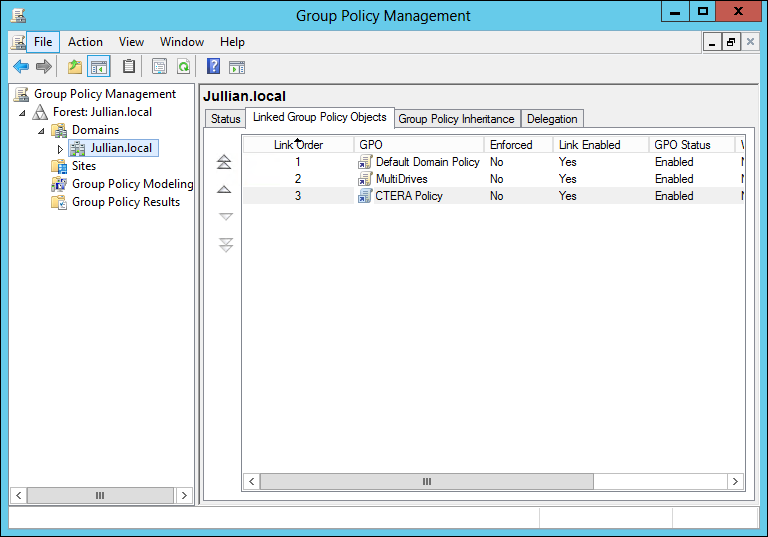
d Double-click the policy to display the policy.
Note: If a Group Policy Management Console message is displayed, click OK.
The policy details are displayed:
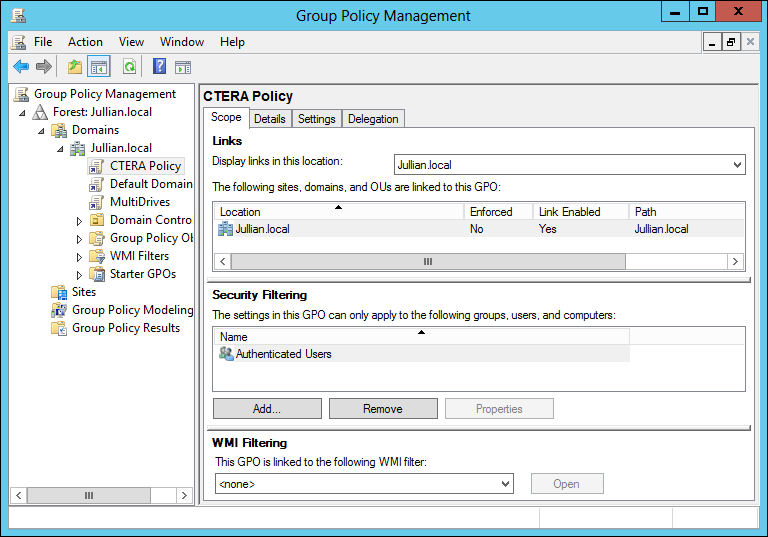
e Right-click the policy you created and select Enforced.
f Right-click the policy you created and select Edit.
The Group Policy Management Editor is displayed.
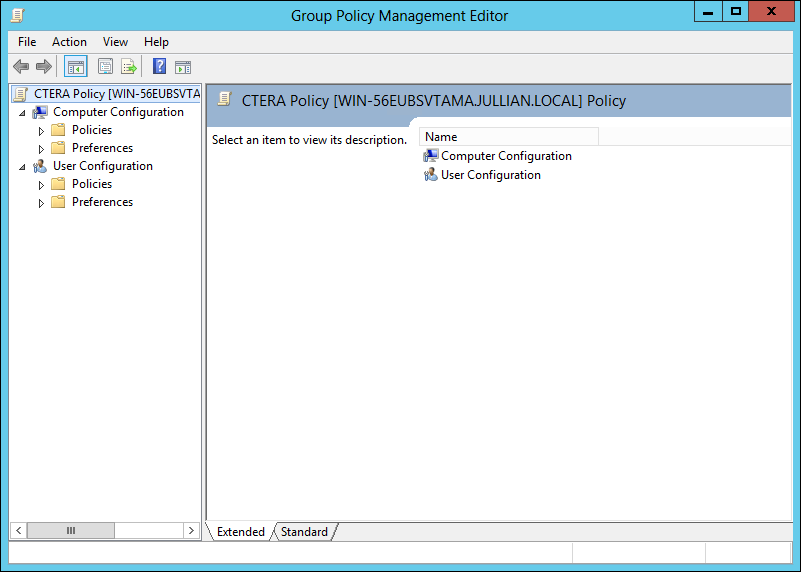
g In the navigation pane, expand Computer Configuration > Policies, right-click Administrative Templates and select Add/Remove Templates.
The Add/Remove Templates window is displayed.
i Click Open.
j Click Close.
k In the navigation pane, expand Computer Configuration > Policies > Administrative Templates > Classic Administrative Templates and click the CTERA Agent Settings node.
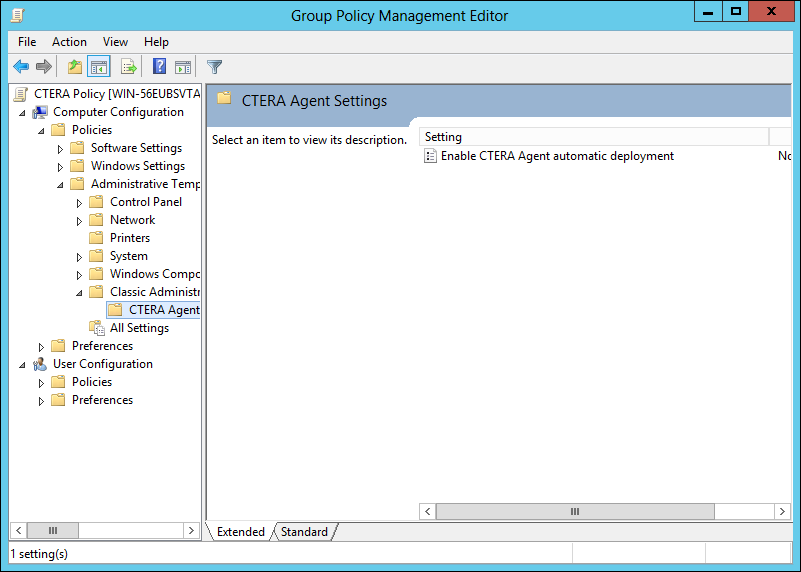
l Right-click Enable CTERA Agent automatic deployment and select Edit.
The Enable CTERA Agent automatic deployment window is displayed.
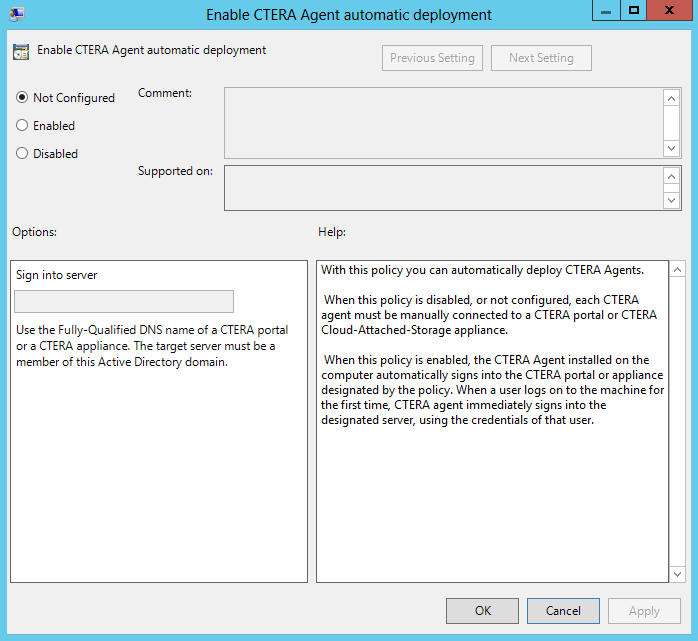
m Specify the following:
Enabled – Set the Enabled option.
Sign into server – Type the fully qualified DNS name of the CTERA Portal to which the CTERA Agent will connect. For example, myportal.ctera.com.
n Click OK.
3 In the Start menu on the server where Active Directory runs, select Administrative Tools > Active Directory Users and Computers.
a Right-click on the name of the domain to which you want to add the user and click New > Organizational Unit.
The New Object - Organizational Unit window is displayed.
b Enter a name for the unit and click OK.
c Right-click on the organizational unit and click New > User.
The New Object - User window is displayed.
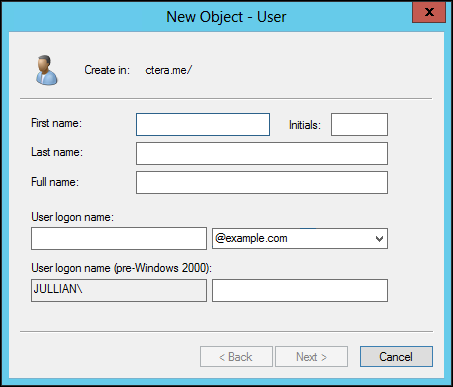
d Fill in the user details: In the User logon name area, in the first field enter a user account, such as cteraportal, and in the second field select the domain.
e Click Next.
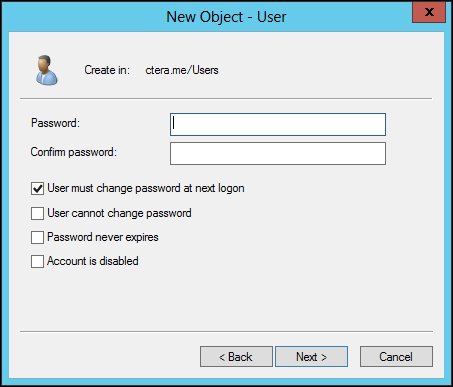
f In the Password and Confirm password fields, enter a password for the user.
The password must be at least 8 characters in length and conform to at least 3 out of the following 4 requirements:
g Clear the User must change password at next logon check box.
h Check the User cannot change password and Password never expires check boxes.
i Click Next.
The summary for the new user is displayed.
j Click Finish.
4 Map the service principal name to the user account that you created and generate a keytab file, by running the following command on the domain controller:
ktpass –princ SPN -out path_to_keytab -mapuser account_name@DOMAIN -mapOp set –pass account_password
Where:
For example: cttp/portal.example.com@example.com
The SPN syntax is cttp/portal_full_DNS_name@ACTIVE_DIRECTORY_REALM
Note: The Active Directory Kerberos realm must match the CTERA Portal's DNS suffix. The email pattern must include only uppercase letters.
For example, c:\cteraportal.keytab.
Note: The keytab file name must include only uppercase letters.
For example, DOMAIN.LOCAL
The domain name must include only uppercase letters.
For example, cteraportal.
For example, Password12E4.
For example:
ktpass -princ cttp/”SERVER FQDN”@”DOMAIN FQDN” -mapuser ctera_portal@”DOMAIN FQDN” -mapOp set -pass PASSWORD -out c:\temp\ctera_portal.keytab
5 Change network security under local group policy on Active Directory and the CTERA Agent workstation.
To configure Kerberos for single sign on with CTERA Portal:
default_tkt_enctypes = aes256-cts-hmac-sha1-96
default_tgs_enctypes = aes256-cts-hmac-sha1-96
To configure SSO on the portal:
Note: Part of this procedure includes stopping the portal, which will result in some downtime.
1 Enable the keytab file on the CTERA Portal:
a Log in to the CTERA Portal as root, using SSH.
b Run the following command to stop the portal:
c Copy the keytab file from the Active Directory server to /usr/local/ctera/apache_tomcat on the CTERA Portal server.
d Run the following command: ctera-keytab.sh keytabfile where keytabfile is the full name and path of the keytab file.
e Run the following command to start the portal: ctera-portal-manage.sh start
2 Add the Active Directory server to the CTERA Portal:
a Log in to the portal user interface.
b In the virtual portal administration view, select Settings in the navigation pane.
Note: Only one virtual portal can be defined with single sign-on using Kerberos.
c Select Directory Settings, under USERS in the Control Panel content page.
The Directory Services page is displayed.
d Click Settings.
The Directory Services Settings window is displayed.
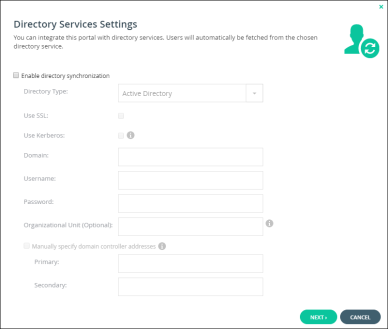
e Specify the following:
Check Enable directory synchronization.
In Directory Type, select Active Directory.
Check Use Kerberos.
In Domain, enter the Active Directory domain.
In Username, enter the username for the Active Directory URL.
In Password, enter the password for the Active Directory URL.
f Click NEXT to the end of the wizard.
g Click FINISH.
SSO is now configured on the CTERA Portal.
Note: A single virtual portal can be configured to enable simultaneous SSO access via both Kerberos SSO and WebDAV SPNEGO, described in Enabling WebDAV Access Without Additional Authentication (Using SPNEGO). For details, see Using Kerberos and SPNEGO Together.